Audit Event¶
From the Audit Event screen, you can download audit logs, enable/disable the audit service, configure remote Syslog server, and limit local audit log storage.
Permission¶
Only users with admin or security officer role can see the Audit Event. Besides that, even the device co-admin user cannot see this page. See here for information on how to create and edit user groups.
NOTICE
Important If Industrial Edge Device remote SSH is enabled, audit logs may have the risk of being modified.
Overview¶
Below is an overview of the Audit Event UI.
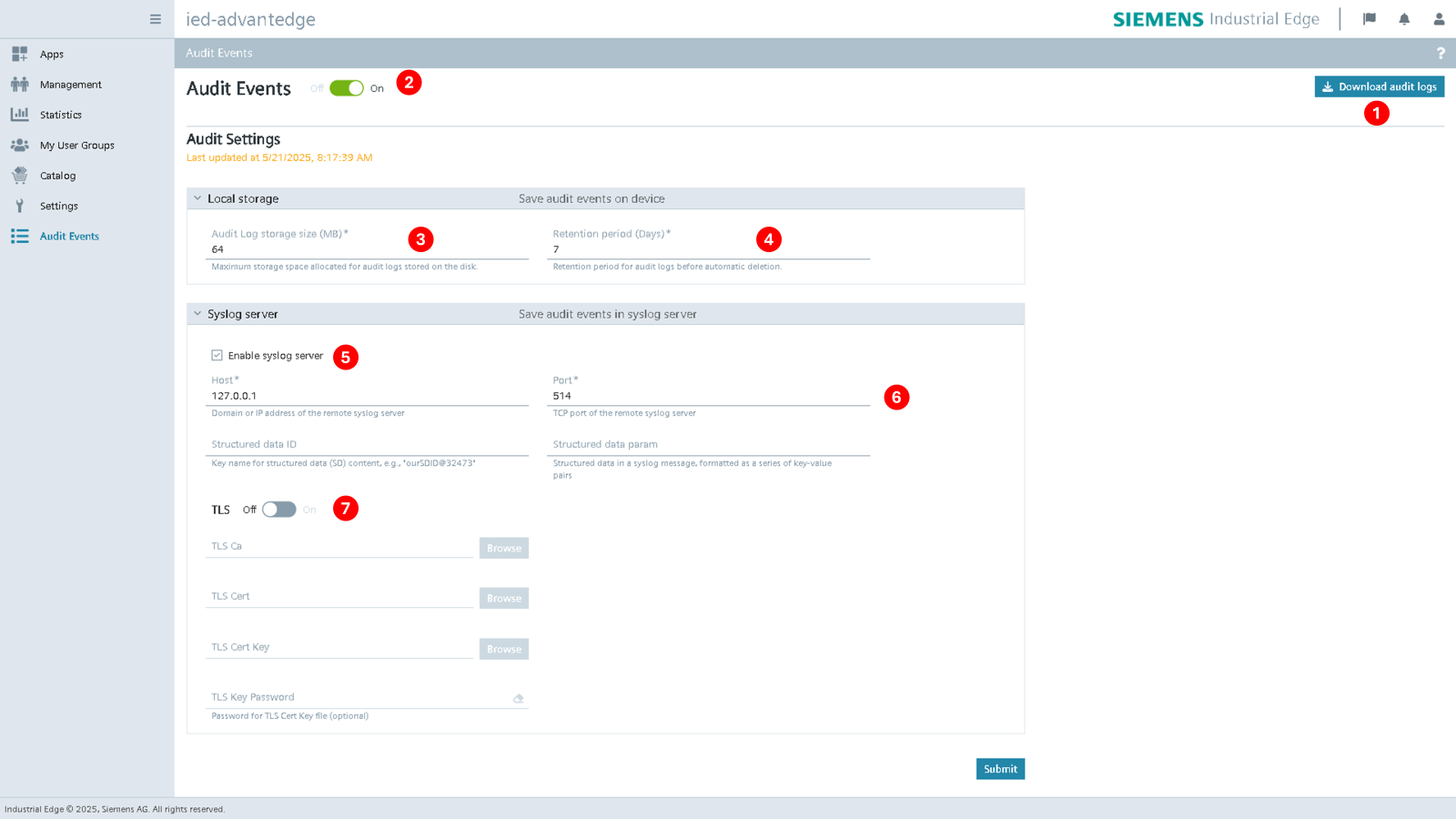
| No. | Items |
|---|---|
| ① | Click to download the audit logs as a .tar archive. The archive contains rotated log files. |
| ② | Enable/disable audit service. If disabled, audit logs are no longer recorded. |
Example in downloaded .tar archive file content:
- One of the rotated files:
-
audit.log-20250206-1738842431
-
An audit event in this file:
{
"appName": "metrics-agent",
"device@4329.6.100.6": {
"FWVersion": "1.21.0-5",
"devID": "c727e0c09f1f44caa3a731aeed78877b",
"devName": "IED",
"devProduct": "Edge Device",
"devVendor": "Siemens"
},
"eventID": "ID58",
"eventType": "SE_AUDIT_CFG_CHANGED",
"function@4329.6.100.6": {
"fct": "ie.device.software.metrics.configuration.update",
"result": "success"
},
"hostName": "10.1.31.103",
"message": "update settings to : flush=5 intervalSec=5",
"session@4329.6.100.6": {
"src": "119.161.122.17",
"userName": "iem.user@siemens.com"
},
"severity": 5,
"severityType": "NOTICE",
"timestamp": "2025-02-06 05:20:21.956200373 +0000 UTC",
"userName": "iem.user@siemens.com"
}
Settings¶
| No. | Items |
|---|---|
| ③ | Set the maximum storage size for audit logs (in MB). The allowed range is 16MB (minimum) to 512MB (maximum), with a default of 64MB. By default, audit logs are stored in /data/audit/log and the active log file (audit.log) is rotated when it reaches 8MB in size or daily, whichever comes first. If the total directory size exceeds the configured maximum storage size limit, old logs will be automatically deleted. |
| ④ | Set the retention period for audit logs (in days). The allowed range is 1 day (minimum) to 30 days (maximum), with a default of 7 days. The audit log files are rotated based on the number of days, and the rotation is "smart", meaning it automatically removes the oldest files when either the maximum storage size or the retention period is reached, whichever comes first. |
| ⑤ | Enable/disable Syslog server. If enabled, audit logs are forwarded to a remote Syslog server using the RFC5424 protocol. Default is disabled. Currently, only Syslog server is supported. |
| ⑥ | The default output port is TCP/514. The Structure data ID and Structure data param fields allow user to fill in an SD-Element object according to RFC5424, if a valid SD-Element is submitted, it will be appended to all audit events before being sent to the Syslog server. |
| ⑦ | Enable/disable TLS verification for the remote Syslog server. The default is disabled. |
Confirmation Dialog Popup¶
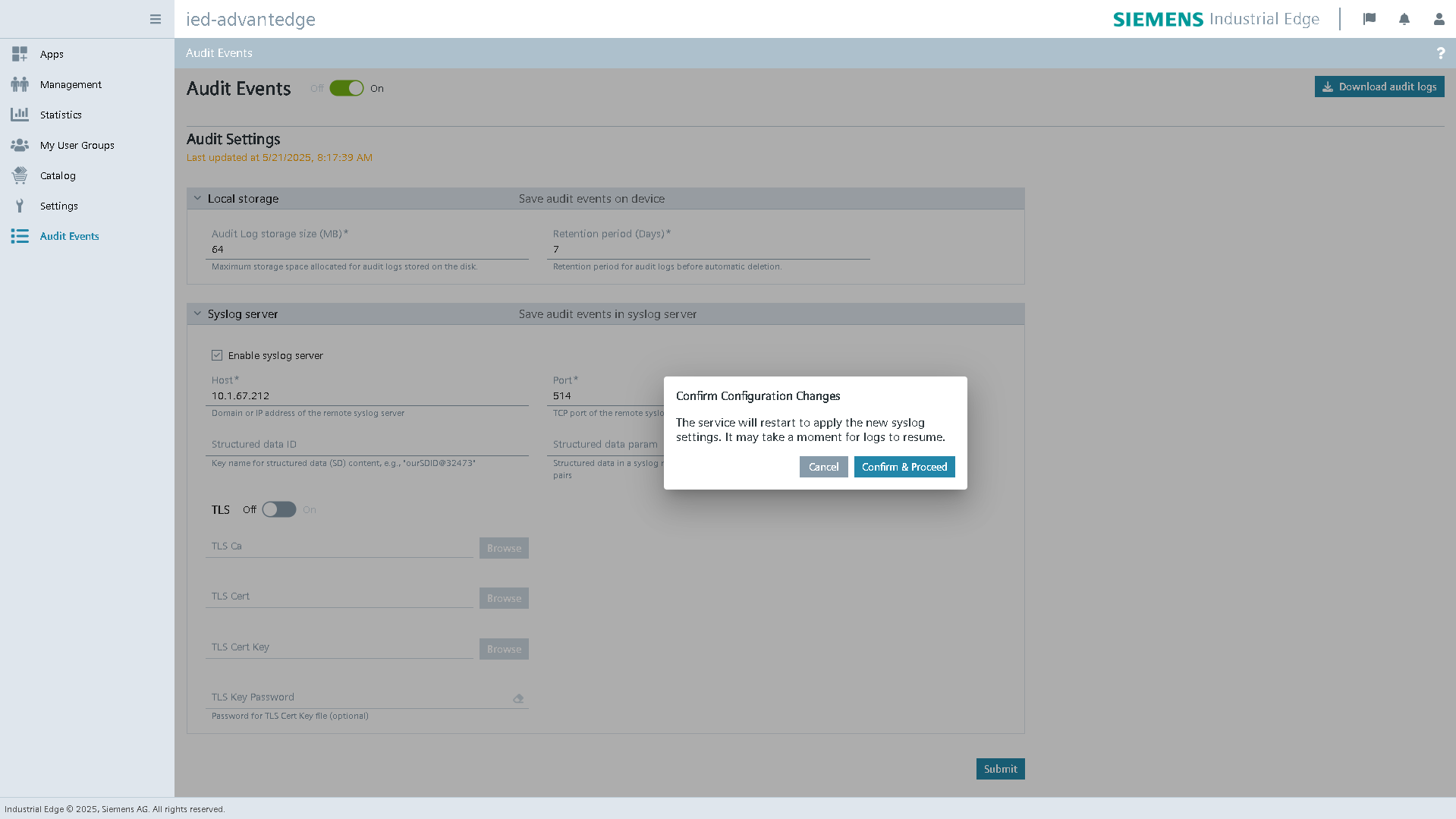
When reducing the Audit Log storage size or Retention period, a confirmation popup is displayed before applying the changes. This popup warns that older audit logs may be permanently deleted and the action cannot be undone. Users are given the option to download existing logs as a .tar archive before proceeding or cancel the operation.
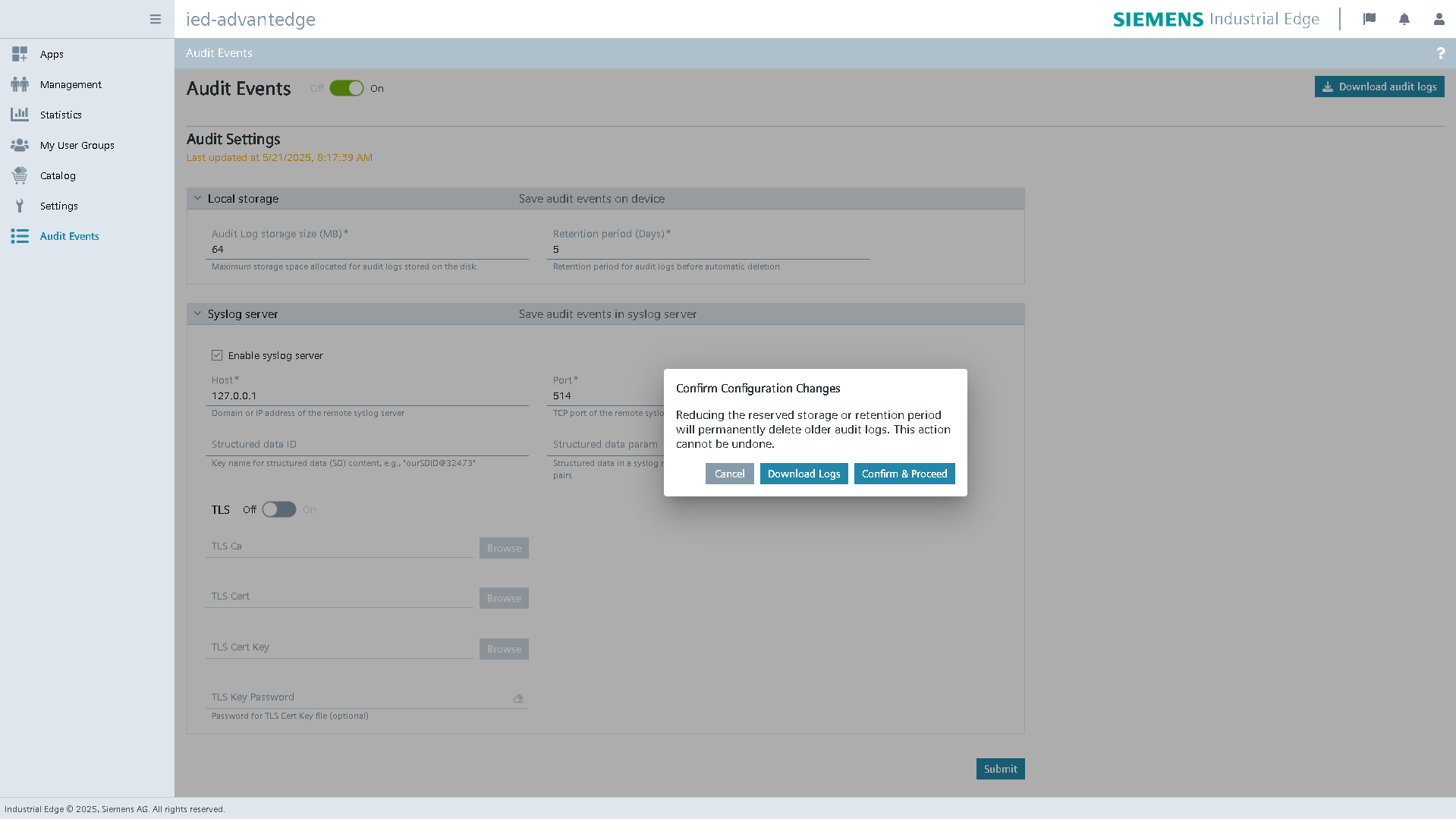
When the Syslog server settings are changed and a Fluent Bit restart is required, a confirmation popup is displayed to inform the user that log forwarding may be briefly interrupted immediately after the restart. This message helps set clear expectations by notifying users of a potential short-term disruption in log delivery during the reconfiguration process.
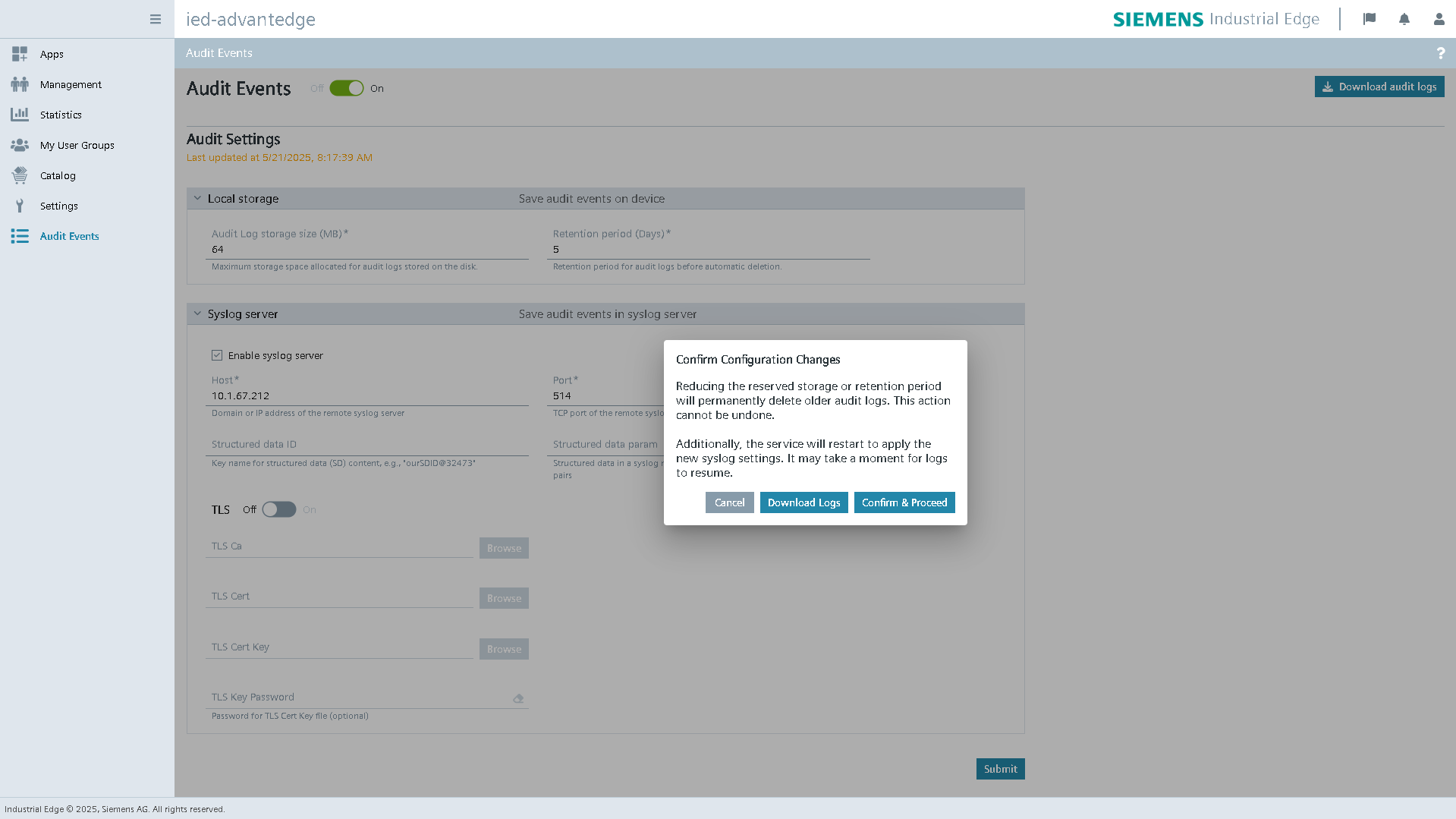
When both local storage settings and Syslog server settings are changed at the same time, a single confirmation dialog displays both warnings. It informs the user that older audit logs will be permanently deleted and that log sending may be temporarily paused due to the Fluent Bit restart. This ensures the user is fully aware of the impact before confirming the changes.
Service and Event Status Notifications¶
Below are the service, event recording, and event streaming status changes as displayed in the Recent Events panel and detailed in the following table. These notifications help Security Officers quickly understand the current operational state of the audit service and identify potential issues.
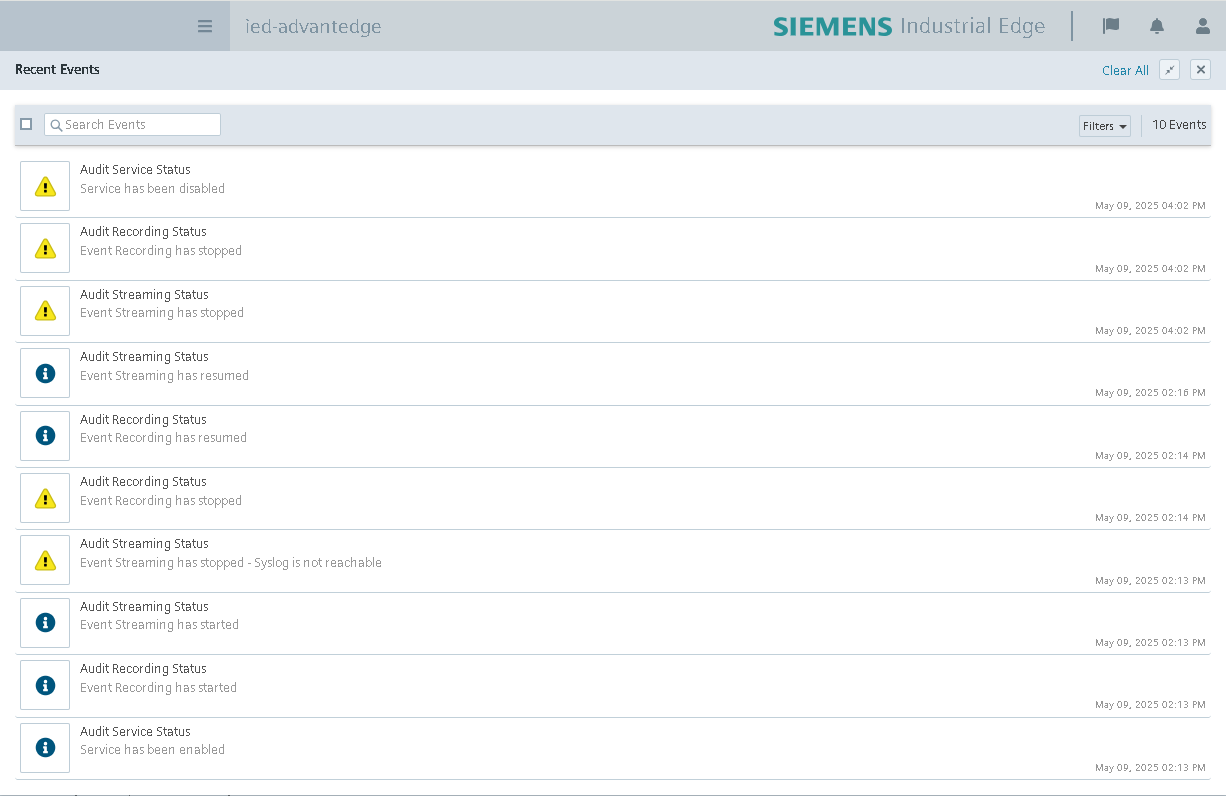
The following table summarizes key status messages related to the audit service, event recording and event streaming activities.
| Title | Message | Description |
|---|---|---|
| Audit Service Status | Service has been enabled | The audit service has been successfully activated and is operational. |
| Service has been disabled | The audit service has been deactivated and is no longer processing events. | |
| Audit Recording Status | Event Recording has started | Event recording has been successfully initiated and is capturing events locally. |
| Event Recording has resumed | Event recording has resumed after a temporary interruption and is continuing to capture events. | |
| Event Recording has stopped | Event recording has stopped, possibly due to internal service failure or configuration issues. | |
| Audit Streaming Status | Event Streaming has started | Event streaming has been successfully initiated, and audit events are being processed and forwarded as configured. |
| Event Streaming has resumed | Event streaming has resumed after a temporary interruption. Events are once again being delivered. | |
| Event Streaming has stopped | Event streaming has been halted, possibly due to a system misconfiguration or internal failure. | |
| Event Streaming has stopped - Syslog is not reachable | Event streaming has stopped because the system could not reach the configured Syslog server or the Syslog settings are invalid. |
Syslog Message Format¶
Example of a Syslog message with structured data (RFC5424 format) forwarded to a Syslog server:
<110>1 2024-08-13T05:20:18.006201Z 10.1.31.103 authservice - ID5 [device@4329.6.100.6 FWVersion="1.21.0-5" devID="c727e0c09f1f44caa3a731aeed78877b" devName="IED" devProduct="Edge Device" devVendor="Siemens"][function@4329.6.100.6 fct="ie.device.software.user.logout" result="success"][session@4329.6.100.6 src="" userName="iem.user@siemens.com"] user: iem.user@siemens.com log out success
Syslog Structure Explanation¶
| Syslog Field | Parameter | DataType | Description | Value Example | ||
| HEADER | PRI | STRING[3..5] | As described in RFC5424, the PRI value should be calculated by facility and severity. For Industrial Edge Device audit event, it should between 104 ~ 111. | 110 | ||
| TIMESTAMP | STRING[20..32] | The TIMESTAMP format that indicates when the event happened. | 2024-05-11T22:14:15.003Z | |||
| HOSTNAME | STRING | The HOSTNAME indicates the Industrial Edge device IP address. | 192.168.19.136 | |||
| APP-NAME | STRING | The APP-NAME indicates where the audit event occurred. | edgesdk | |||
| PROCID | STRING(1 128) | Not in use now. | ||||
| MSGID | STRING(1..32) | The security event Type ID that is defined on Industrial Edge security event website. | ID5 | |||
| STRUCTURED-DATA | SD-ID | device@<ProductOwnID> | STRING(1..32) | This structure-data field provides metadata of the device; 4329.6.100.6 is organization code, you will use your own code. | device@4329.6.100.6 | |
| SD-PARAM | FWVersion | UTF-8 STRING | The firmware version. | 1.19.0-3 | ||
| devID | UTF-8 STRING | The Industrial Edge device ID. | 32803b78dbe6499c8437e962d378a8eb | |||
| devName | UTF-8 STRING | The Industrial Edge device name. | IEDevice001 | |||
| devProduct | UTF-8 STRING | This field indicates the type of device. For Industrial Edge Device it is 'IE Device'. | Edge Device | |||
| devVendor | UTF-8 STRING | It is always 'Siemens'. | Siemens | |||
| SD-ID | function@<ProductOwnID> | STRING(1..32) | This structure-data field provides metadata of the event process; 4329.6.100.6 is organization code, you will use your own code. | function@4329.6.100.6 | ||
| SD-PARAM | fct | UTF-8 STRING | The fct field indicates the function related to the audit event. This field sometimes has additional information. For example, if a user download a security log file, the fct value would be '...download' and the resource value is the name of file. | ie.device.software.app.logs.download | ||
| resource | UTF-8 STRING | This field is associated with the fct field and usually indicates the resource which handled by the function, e.g. filename or protection level. | audit-20240501.log | |||
| result | UTF-8 STRING | It indicates the result (success, failure, loss, return ) of function. | success | |||
| SD-ID | session@<ProductOwnID> | STRING(1..32) | This structure-data field provides metadata of the event session; 4329.6.100.6 is organization code, you will use your own code. | session@4329.6.100.6 | ||
| SD-PARAM | src | UTF-8 STRING | The source client IP address. For example, if the event is caused by user logout, the src value should be the user browser IP. | 23.106.129.48 | ||
| userName | UTF-8 STRING | The username that indicates who operates or causes the event. | username@company.example | |||
| MSG | UTF-8 STRING | The MSG part contains a free-form message that provides information about the event. | user log out | |||
Industrial Edge Audit Event List¶
The following table lists the Industrial Edge audit events.
The fct value of an audit event is a string concatenated by . such as ie.device.software.app.logs.download.
The resource field is an optional field, it indicates the object of the user's actions.
| fct | resource | Security Event Type |
|---|---|---|
ie.device.software.app.logs.download |
<filename> |
SE_DATA_EXPORTED |
ie.device.software.app.start |
SE_APPLICATION_OPERATION | |
ie.device.software.app.stop |
SE_APPLICATION_OPERATION | |
ie.device.software.app.restart |
SE_APPLICATION_OPERATION | |
ie.device.software.app.uninstall |
SE_APPLICATION_OPERATION | |
ie.device.software.app.install |
SE_APPLICATION_OPERATION | |
ie.device.software.app.configuration.update |
SE_APPLICATION_OPERATION | |
ie.device.software.app.configuration.delete |
SE_DELETE_OBJECT | |
ie.device.software.app.configuration.download |
<filename> |
SE_DATA_EXPORTED |
ie.device.software.app.auth.login |
SE_NETWORK_SUCCESSFUL_LOGON, SE_NETWORK_UNSUCCESSFUL_LOGON | |
ie.device.software.app.securestore.update |
SE_APPLICATION_OPERATION | |
ie.device.software.app.securestore.delete |
SE_APPLICATION_OPERATION | |
ie.device.software.app.versions.update |
<versionId> |
SE_APPLICATION_OPERATION |
ie.device.software.device.reboot |
SE_DEVICE_STARTUP | |
ie.device.software.device.shutdown |
SE_CRITICAL_DEVICE_STOPPED | |
ie.device.software.device.statistics.view |
SE_OBJECT_OPERATION | |
ie.device.software.device.cert.upload |
<filename> |
SE_SECURITY_CONFIGURATION_CHANGED, SE_DATA_IMPORTED |
ie.device.software.device.developermode.enable |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.developermode.disable |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.job.execute |
SE_OBJECT_OPERATION | |
ie.device.software.device.job.delete |
SE_DELETE_OBJECT | |
ie.device.software.device.logs.download |
<filename> |
SE_DATA_EXPORTED |
ie.device.software.device.logs.update |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.device.ntp.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.ports.view |
SE_OBJECT_OPERATION | |
ie.device.software.device.proxy.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.remoteaccess.enable |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.remoteaccess.disable |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.ramlimit.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.time.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.thresholdlimit.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.network.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.discovery.reset |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.device.hardreset |
SE_RESET_TO_FACTORY | |
ie.device.software.device.softreset |
SE_RESET_TO_FACTORY, SE_MEMORY_RESET | |
ie.device.software.device.notification.update |
SE_OBJECT_OPERATION | |
ie.device.software.device.resource.view |
SE_RECONNAISSANCE_DETECTED | |
ie.device.software.user.profile.update |
SE_OBJECT_OPERATION | |
ie.device.software.user.login |
SE_NETWORK_SUCCESSFUL_LOGON, SE_NETWORK_UNSUCCESSFUL_LOGON | |
ie.device.software.user.logout |
SE_LOGOFF | |
ie.device.software.user.approve |
SE_ACCOUNT_ENABLED | |
ie.device.software.user.password.reset |
SE_ACCESS_PWD_CHANGED | |
ie.device.software.user.enable |
SE_ACCOUNT_ENABLED | |
ie.device.software.user.delete |
SE_USER_DELETED | |
ie.device.software.user.group.create |
<groupName> |
SE_USER_GROUP_CREATED |
ie.device.software.user.group.delete |
<groupName> |
SE_USER_GROUP_DELETED |
ie.device.software.user.group.update |
<groupName> |
SE_USER_ACCOUNT_ADDED_TO_GROUP, SE_USER_ACCOUNT_DELETED_FROM_GROUP |
ie.device.software.user.permission.update |
SE_SECURITY_CONFIGURATION_CHANGED | |
ie.device.software.audit.enable |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.audit.disable |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.audit.configuration.update |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.audit.configuration.delete |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.audit.logs.download |
<filename> |
SE_AUDIT_DATA_SAVED |
ie.device.software.audit.logs.view |
SE_OBJECT_OPERATION | |
ie.device.software.state.backup |
SE_BACKUP_STARTED, SE_BACKUP_FAILED, SE_BACKUP_SUCCESSFULLY_DONE | |
ie.device.software.state.restore |
SE_BACKUP_RESTORE_STARTED, SE_BACKUP_RESTORE_FAILED, SE_BACKUP_RESTORE_SUCCESSFULLY_DONE | |
ie.device.software.metrics.enable |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.metrics.disable |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.metrics.configuration.create |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.metrics.configuration.update |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.metrics.configuration.delete |
SE_AUDIT_CFG_CHANGED | |
ie.device.software.metrics.configuration.import |
<filename> |
SE_DATA_IMPORTED |
ie.device.software.metrics.configuration.export |
<filename> |
SE_DATA_EXPORTED |
ie.device.software.metrics.configuration.check |
SE_COMMUNICATION_DATA_INTEGRITY_ERROR | |
ie.device.software.resourcemanager.configuration.update |
SE_CFG_DATA_CHANGED |