Issues and Solutions¶
- User email is not verified
- Access Denied
- Warning when disabling Identity Federation
- Redirect URI error
- Local login for users with Device Admin role
- Incompatible Devices
- No applications displayed on the device dashboard after logged in
- Device removed or reset before disabling Identity Federation
- Invalid Credentials error after performing a Soft Reset
- Session expired error if user isn't permitted for Enable / Disable Identity Federation
- Failed Identity Federation Job after a previous Identity Federation job doesn't run successfully
- Known limitations
User email is not verified¶
The following error message indicates that the user trying to login does not have a verified email address on the IEM.
Linking of user¶
As described in the section Identity Federation and how does it work, assuming required criteria is fulfilled, the user will be linked to an existing device user which matches the provided email. In case the user did not exist on the device, a new user will be created and linked. The user email address serves as unique identifier, therefore at the moment of the login attempt, the email verification should have already taken place. To enhance security and prevent unauthorized access, we have implemented additional measures for email verification.
There are two ways to ensure email verification:
SMTP Verification¶
Your system administrator needs to add a valid SMTP server to send a verification email to the user. Users will be required to verify their email address through SMTP. This process involves sending a verification email to the provided address. Upon receiving the verification email, users must follow the instructions to confirm their email address. Only verified email addresses will be eligible for automatic linking and access to IEDs.
Manual Verification by IT Administrator¶
For an added layer of security, Your system administrator (with IAM access) will also manually verify email addresses upon user registration or account modification.
Unverified email addresses will not be granted access to the system until the verification process is completed. For further information on how to configure see here.
Access denied¶
This error message is the expected behavior, ensuring that only users with the corresponding role are allowed to access the device, via IEM Identity Federation. If you get this message please contact your system administrator to assign one of the device roles, thus, granting you access to the Device.
Warning during Disable Identity Federation Job¶
When disabling Identity Federation, the following hint can appear after the job successfully ran.
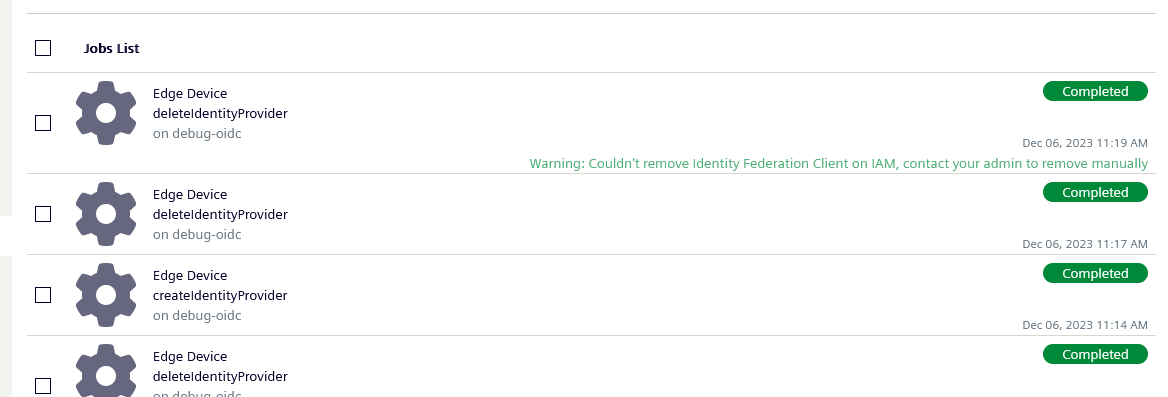
This is a hint, indicating that between enabling and disabling, some manual configuration was done on client side, which could lead to some issues, when disabling the Identity Federation. If you get this error, your system should still work as expected, but it is recommend to be checked by your system administrator.
Redirect URI¶
When you receive an Error during Login "Invalid Redirect URI", most probably your device has been assigned a new IP Address (or is reachable only via DNS name). In this case, ask your system administrator to manually update the address under "Valid redirect URIs".
Local Login for Users with Device Admin Role¶
It is currently not possible to reset the Password of a Device Admin. Therefore if you want to enable Local Login for an Admin User, you need to follow these steps:
- Assign the User Role on the IAM, to the user you want to grant local login.
- Login with the user, this will update the user role to
Userin the device. - Using a device Admin, get the user token to reset the password.
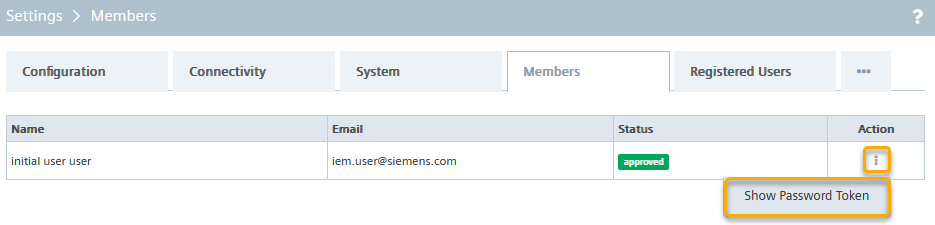
- On the device, reset the password of your user with the extracted token.
- Assign back the Admin Role to your user on the IAM(optional).
After the user logs in again using Identity Federation, it should be allowed to login locally with admin rights.
Identity Federation Incompatible Devices¶
The feature is only with devices which have the IE Runtime version 1.17.0-n or higher, for other runtime versions the job will be skipped with the following Warning.

If you get this message contact your system administrator to update the firmware of your device, up to a version which supports Identity Federation.
No applications displayed on the device dashboard after logged in¶
In case you have successfully logged in and you see no applications on the device dashboard (see image below).
NOTICE
This is expected behavior. It indicates that your user has the User role on the Device, however it does not belong to any user groups in the Device, therefore not getting any applications displayed on the app overview. The applications offering a UI can however still be reached directly even with the User role.
You can contact a user with Admin role, to assign you to a user group. For users with the Admin role, the device dashboard will display all applications without the need to belong to any user groups.
Device removed or reset before disabling Identity Federation¶
Removing a device from the Industrial Edge Management, when the device had the Identity Federation enabled, will not automatically remove the Identity Federation components, neither on the IAM nor on the Device. There are three scenarios where this can happen:
- The device was manually removed on the IEM.
- A Hard Reset was triggered for the device.
- Reset (formerly known as soft reset) was triggered for the device.
Scenario 1¶
In case the device was removed on the IEM, the device will be removed from the Industrial Edge Management device view. You should be aware that, device users which also exist on the IAM system, will still be able to use Identity Federation, since the device is reachable locally and the IAM client is not deleted upon device removal.
Therefore we recommend to remove the leftovers manually as follows (IAM access is required):
- Go to your IAM.
- On the left panel, click on
Clients. - Look for the client corresponding to your device, the name should be
ie-device-<your device name>. - Click on the three dots icon on the right and select
Delete.
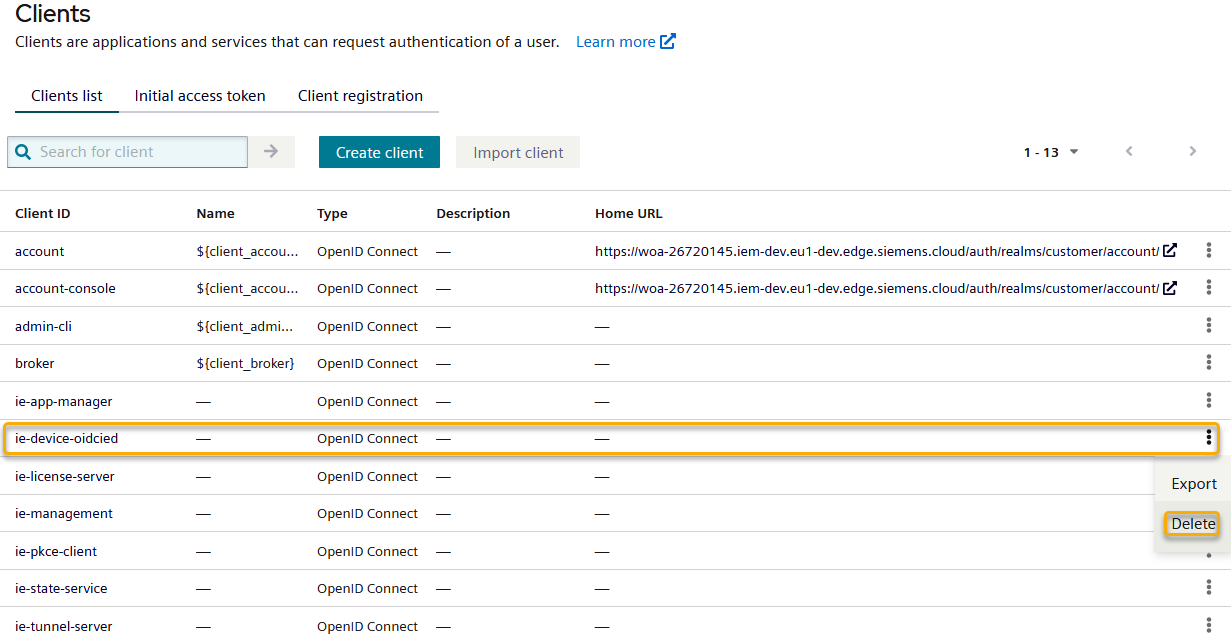
Additionally it is necessary to perform a hard reset on the device, since it is no longer part of the IEM. This way you can onboard the device to an IEM and the OIDC providers will also be removed from the device.
Scenario 2¶
When a Hard Reset has been done on the device side, the device will remove all the OIDC providers and Identity Federation information. However on the IEM side, the IAM client will not be automatically removed, therefore, similar to scenario 1, the device client should be removed manually.
- Go to your IAM.
- On the left panel, click on
Clients. - Look for the client corresponding to your device, the name should be
ie-device-<your device name>. - Click on the three dots icon on the right and select
Delete.

Scenario 3¶
A device reset will keep the device as part of the Industrial Edge Management. However the OIDC provider from your device would have been removed, leaving leftovers behind on your IAM. In order to cleanup the IAM you can simply go to the device view in the UI and disable the Identity Federation (as described in the Disable Identity Federation section).
Invalid Credentials Error after performing a Soft Reset¶
If you get the error "invalid credentials" when trying to login to the device after a device soft reset, it could be that your user had the role User when a soft reset was triggered. During soft reset, all users which are not device Administrators are cleaned up. If you want to recover your user, you can ask a device administrator to create the user for you. Alternatively you can recreate your user via Identity Federation and get local access by following the workflow described on the section Local Login for Users with Device Admin Role.
Session expired error when user is not allowed to Enable / Disable Identity Federation¶
When you enable/disable Identity Federation without sufficient privileges, you receive the following error message
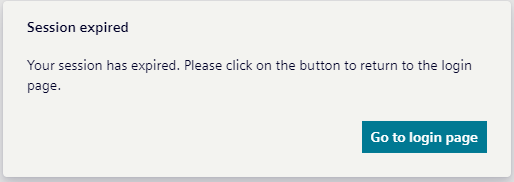
Although the error message states that the session has expired, the user does not have sufficient permissions to enable/disable Identity Federation for the device. If you receive this error, we recommend that you contact your administrator to assign the proper permissions.
Failed Identity Federation job after a previous Identity Federation job did not run successfully¶
If an Identity Federation job fails, a subsequent Identity Federation job will also fail. The following list provides a selection of possible scenarios where this might occur:
- The Identity Federation job was manually deleted before it ran successfully.
- The Identity Federation job failed to execute.
In these cases, the IAM client is not automatically removed, so you must manually remove the device client:
NOTICE
IAM access is required.
NOTICE
Important for IEM Version 1.14.9 Due to a limitation in the underlying Keycloak implementation, clients with composite client roles cannot be deleted directly. If your client has composite roles, you must first remove all of them. This limitation only affects IEM Version 1.14.9.
- Navigate to your IAM.
- On the left panel, click on
Clients. - Look for the client corresponding to your device, the name should be
ie-device-<your device name>. - If using IEM Version 1.14.9:
- Click on the client name
- Navigate to
Rolestab - Remove all composite roles
- Click on the three dots icon on the right and select
Delete.
Known Limitations¶
- Identity Federation over Remote Access is only supported for Industrial Edge Management App version 1.17.n or higher, in combination with a device containing the IE runtime version 1.18.0-n or higher.
- Redirect URIs must be manually changed on IP change of Device.
- Devices reachable via DNS name, the name address of the Device should be manually added to the Redirect URIs.
- Users are not automatically added to invited groups.



