Certificate Management in the Industrial Edge Ecosystem¶
Certificates are essential for securing communication and establishing trust between various components in the Industrial Edge Ecosystem. These certificates are managed slightly differently across the various Industrial Edge Management (IEM) offerings. Certificates are essential for securing communication and establishing trust between various components in the Industrial Edge Ecosystem. These certificates are managed slightly differently across the various Industrial Edge Management (IEM) offerings.
NOTICE
For further information on certificate management for the Industrial Edge Management (IEM) and the Industrial Edge Device (IED), please refer to the following resources:
The role of IEM in secure communication¶
IEM provides an HTTPS endpoint for device and user communication (via browser). To establish secure communication, a chain of trust must be configured. This involves updating the client's certificate store (whether on a PC, browser, or device) with the root certificate employed by the IEM.
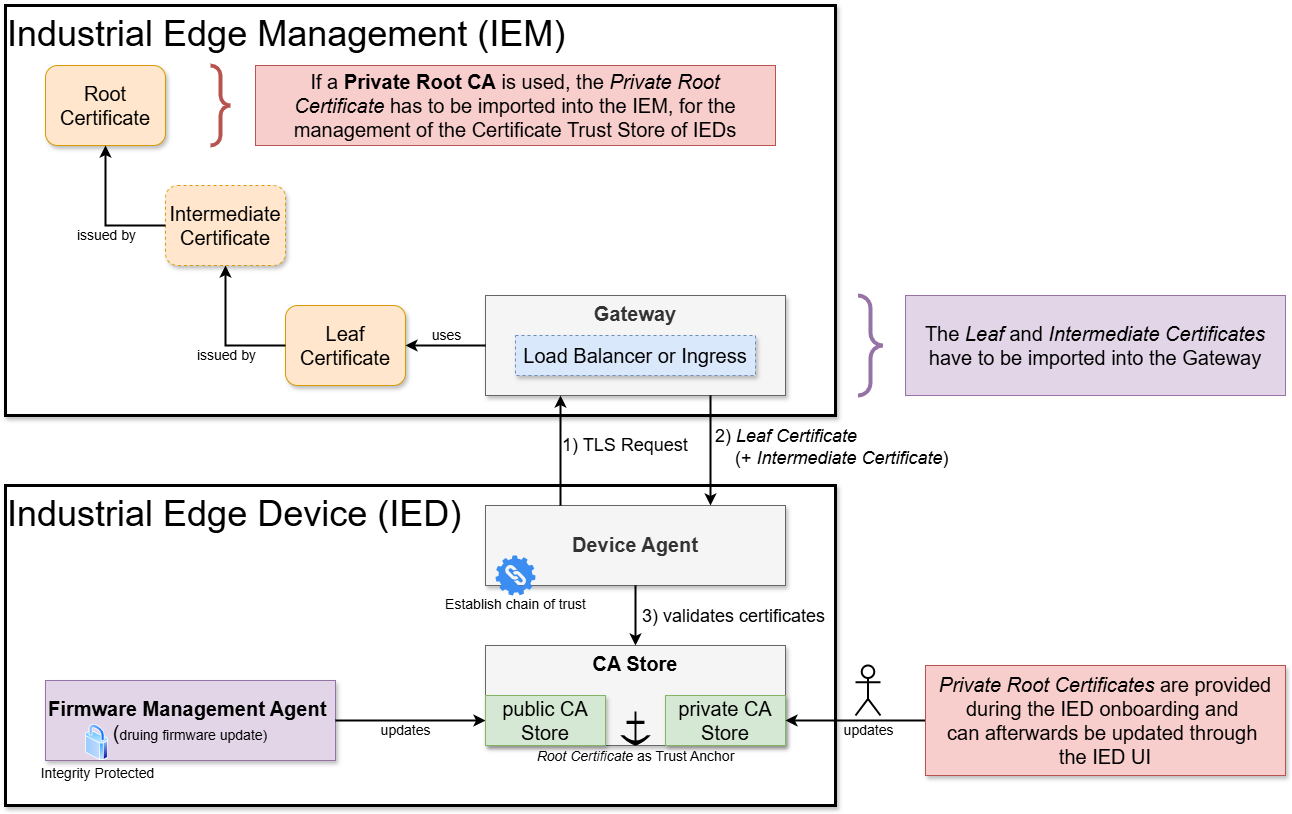
Chain of trust explained¶
A chain of trust is a security model that verifies the authenticity and integrity of a certificate. It begins with a trusted root certificate issued by a Certificate Authority (CA) and often includes an intermediate certificate, which links the root certificate to the end-user certificate. Each certificate in the chain validates the next one, ensuring that the connection remains secure.
When a device or browser establishes a connection, it checks the entire chain - root, intermediate, and end-user certificates - confirming that each certificate is valid and ultimately trusted by the root CA.
Certificate lifecycle management¶
Certificates follow a defined lifecycle that includes issuance, use, expiration, and renewal or revocation. Key aspects of this lifecycle include:
- Expiration Time: Regular certificates (e.g., server or device certificates) usually have shorter expiration times of one to two years to ensure outdated or potentially compromised certificates are frequently renewed. In contrast, root certificates have longer expiration times of 10 to 25 years to maintain stability in the chain of trust, as they serve as the foundation for many devices and systems globally.
NOTICE
For further information on certificate management on the Industrial Edge Management (IEM), please refer to: Certificate Management on the IEM
Understanding public trust stores and private root certificates in IEDs¶
Industrial Edge Devices (IEDs) utilize a public trust store to verify certificate authenticity during HTTPS communications. This store is a collection of trusted root and intermediate certificates from recognized Certificate Authorities (CAs), pre-installed on most devices and browsers. Public root certificates allow IEDs to securely connect to external services without additional configuration.
Moreover, IEDs support the integration of private root certificates, enabling organizations to utilize a corporate Public Key Infrastructure (PKI). This feature facilitates secure internal communication within private networks, allowing devices and services to authenticate using a custom Certificate Authority (CA) for enhanced security and flexibility.
Managing certificate stores on IEDs¶
Effective management of the certificate store on IEDs is critical for secure communication. This process varies based on whether the device uses the public trust store or a private root certificate chain:
-
Public Trusted Certificates: The public trust store is automatically managed via firmware updates, ensuring the latest trusted root and intermediate certificates are maintained without manual intervention.
-
Private Root Certificates: When using a private root Certificate Authority (CA), the root certificate is provided as part of the onboarding file. This root certificate is added to the internal trust store, allowing validation of Industrial Edge Management (IEM) certificates against the private root Certificate Authority (CA) during communication.
Certificate import guidelines¶
When using a private root certificate in an Industrial Edge environment, it is important to handle the certificates correctly in both Industrial Edge Management (IEM) and on the Industrial Edge Devices (IEDs). The private root certificate can be uploaded to the IEM either during the initial provisioning or during certificate rotation. Doing so allows the certificate to be automatically distributed to the device trust stores while onboarding, ensuring secure communication.
-
Certificate chain: If the certificate chain includes intermediate certificates that are not already included in the IEM API Gateway, they must be provided together with the root certificate as part of a complete and correctly ordered certificate chain.
-
Common Name (CN): Should represent the primary domain of the web server (e.g., CN =
www.example.com). For wildcard certificates, include the wildcard character (e.g., CN =*.example.com). -
Subject Alternative Name (SAN): Must list all domain names the certificate should secure (e.g., DNS:
example.com, DNS:www.example.com). SAN is mandatory for modern browsers.
NOTICE
Certificate file formatting When uploading certificates to IEM or importing them directly to an IED, careful attention to file formatting is required. Some internal libraries will only process certificates if they are formatted correctly. Important: Ensure that all certificate files use LF (\n) for line breaks. Using other line-ending formats (such as CRLF \r\n) may lead to certificate parsing issues and can even cause failures during firmware updates.
Certificate key and algorithm requirements¶
- Key Length: For RSA, use a minimum of 2048-bit key length; for ECC, use curves like P-256 or P-384.
- Algorithm: Use secure hashing algorithms such as SHA-256 or higher; signing algorithms should be SHA-256 with either RSA or ECDSA.
- Key Length: For RSA, use a minimum of 2048-bit key length; for ECC, use curves like P-256 or P-384.
NOTICE
Certificates generated with ECC algorithms can only be used for Industrial Edge Management and not for Industrial Edge Devices.
Certificate validity and renewal¶
- Validity Period: Certificates should have a maximum validity of 1 year (398 days). Shorter validity periods are recommended for enhanced security.
- Renewal: Implement automated certificate renewal processes to avoid service disruptions. Test the renewal process to ensure minimal impact on the web service.
If a private root certificate is used and the root certificate is changed after the onboarding of the Industrial Edge Devices (IED), ensure that the new root certificate is imported to the IED to maintain trust and secure communications. Checkout Manage IED Certificate Trust Store for more details.
NOTICE
For further information on certificate management on the Industrial Edge Device (IED) checkout: Certificate Management on the IED
Summary of certificate types¶
Public trust store¶
- Contains certificates from publicly recognized CAs.
- Pre-installed on most devices, browsers, and operating systems.
Private root certificate chain¶
- Used within closed, private environments such as IEM.
- Issued by an organization's private CA, requiring manual addition to devices' trust stores.
- Ensures secure communication in controlled environments, not trusted by default on external devices.