Installation of Device Applications¶
For the installation of Device Applications two different scenarios with separate starting points can be differentiated:
- Installing one application on one or multiple devices: Start from the Device Application details page
- Installing one or multiple applications on one device: Start from the Device details page
NOTICE
It is not possible to install multiple applications on multiple devices in one go.
After the initial selection of applications and devices, the installation process follows a similar workflow.
Installing one application on multiple devices¶
You can install any application on one or more compatible devices:
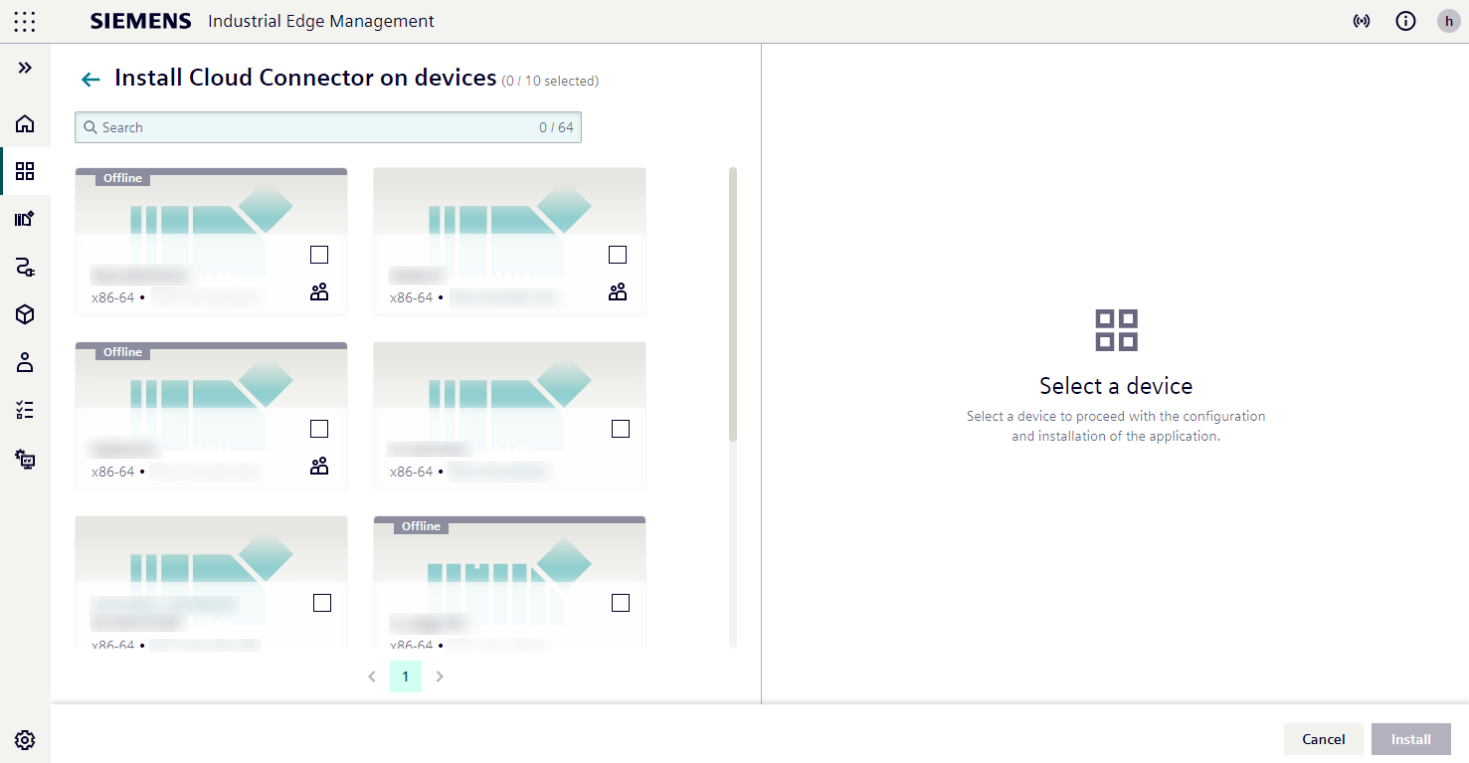
- Select from the list of devices that match the application's architecture
- Selected device cards become highlighted
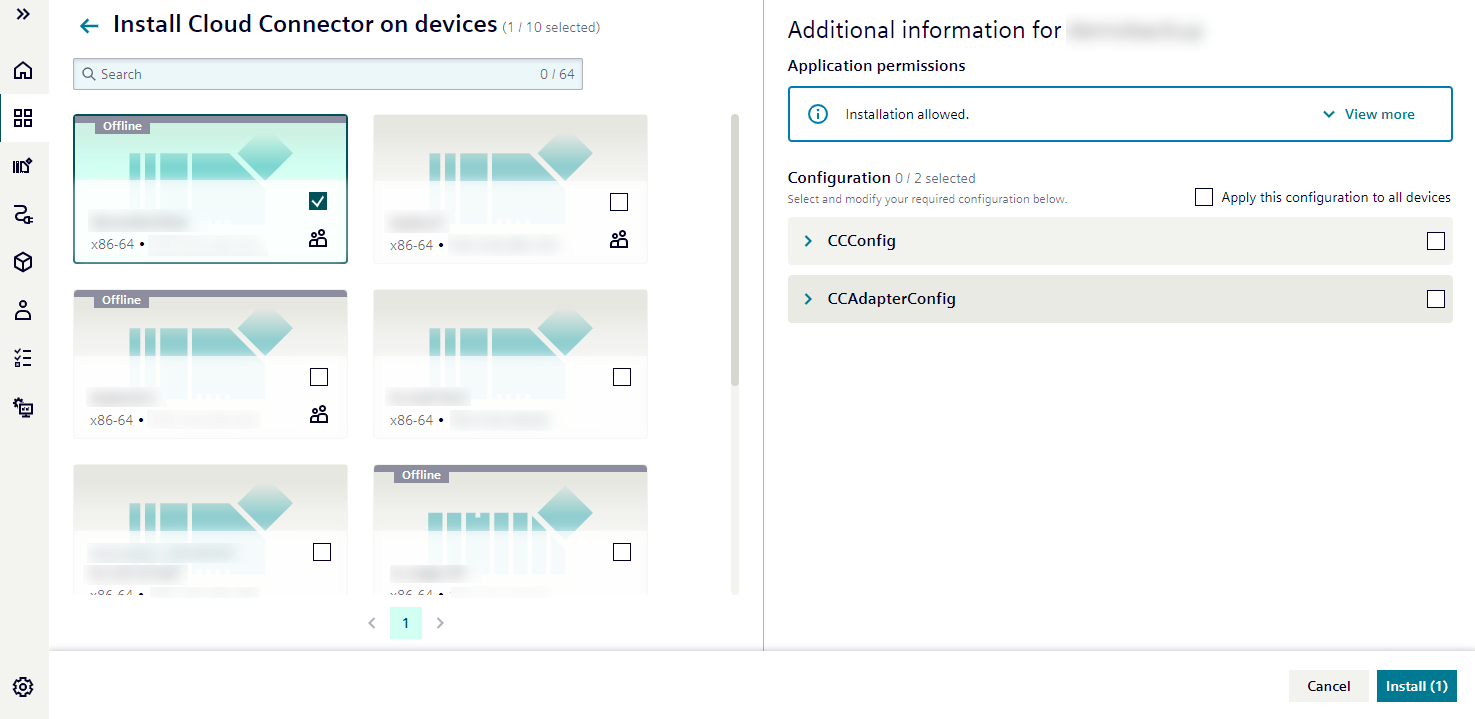
- An information panel appears on the right showing:
- Application permissions
- Configuration options specific to the selected device
- To configure a different device, simply change the device selection on the left. Different configurations apply for selected devices
Installing multiple applications on one device¶
You can install multiple compatible applications on a single device:

- Select from the list of applications that match the device's architecture
- Selected application cards become highlighted
- An information panel appears on the right showing:
- Application permissions
- Configuration options specific to the highlighted application
- To configure a different application, simply click its tile
Application Permissions¶
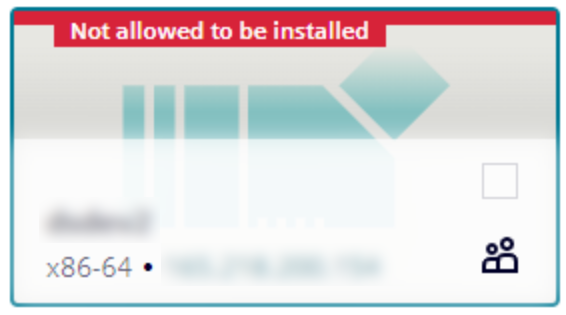
An application can have three types of permissions: Allowed, Warning or Blocked.
If any application has Blocked permissions, the device card will show the label Not allowed to be installed and can not be selected for installation.
Configurations¶
There can be three types of configurations:
-
Version based configuration
-
File based configuration
-
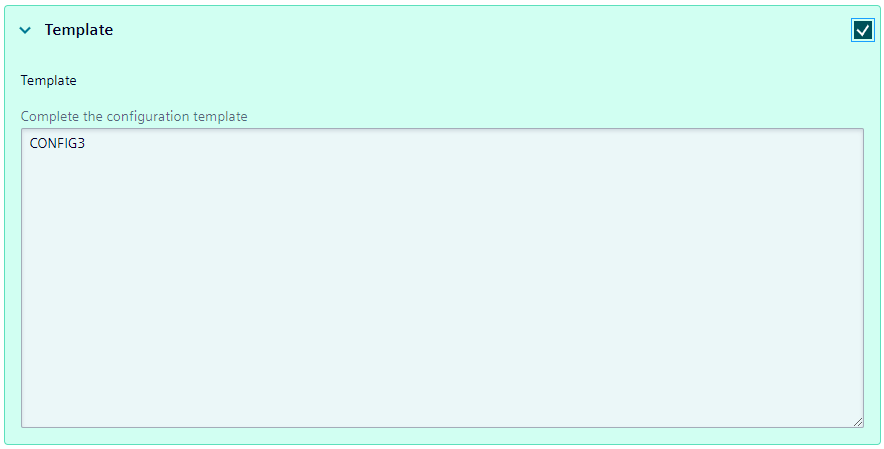
Template based configuration
Apply configurations¶
In order to apply the configurations you need to check the checkbox next to each configuration before the installation.
Upon the installation of one application to many devices, you can easily apply a configuration to all other selected devices by checking the Apply this configuration to all devices checkbox.

NOTICE
You will be prompted for confirmation whenever you attempt to overwrite a previously selected configuration.
Installation submit¶
Once you have selected the application(s) or device(s), you can submit the installation.
When clicking on the Install button you will receive a notification at the bottom right of the screen.

App Validation¶
Before an app is installed on the Industrial Edge Device (IED), the Industrial Edge Management (IEM) system analyzes its configuration and runtime behavior. Users are notified about key aspects such as expected resource claims, requested privileges, and access to networks or volumes.
Unsupported Docker Compose Version
| Code: | compose_version.IED.warn |
| Summary: | This warning indicates that the application is defined using a Docker Compose specification version that is might not be compatible with the Industrial Edge Device (IED). The application might use docker compose features which will not work properly on the device, but the application might still be installable. This might lead to operational inconsistencies. |
| Recommendation: | Update the IED firmware to a version that supports this Compose file, or use a compatible version of the app. |
Privileged App from Unverified Vendor
| Code: | privilege_check.warn |
| Summary: | This warning indicates that the application requests elevated system privileges (e.g., privileged: true) and is not published by a verified or trusted vendor. Such permissions can bypass container isolation and access core system resources.td> |
| Recommendation: | Only proceed if you fully trust the app and vendor. Prefer alternatives from verified sources. |
Access to Sensitive Host Volumes
| Code: | volume_check.warn |
| Summary: | This warning indicates that the application is configured to mount sensitive host directories (e.g., /etc, /var/run, /proc) into the container, potentially giving it access to critical system files. The app may read or modify system configuration and runtime data. Access to host volumes can be exploited to escalate privileges or persist malicious code. Additionally, the application originates from an unverified vendor. |
| Recommendation: | Install only if the source is trustworthy. Otherwise, select an alternative or verify the vendor. |
Use of Host Network
| Code: | host_network.warn |
| Summary: | This warning indicates that the application is configured to use the host network (network_mode: host), allowing it direct access to the network stack of the Industrial Edge Device (IED). The app can monitor or interfere with network traffic, potentially leaking or altering data. |
| Recommendation: | Use only if necessary and if the vendor is known and trusted. |
Host Process Interaction
| Code: | pid_host.warn |
| Summary: | This warning indicates that the application is configured in a way that allows it to interact with host-level processes or execute commands directly on the host system, leading to potential system instability or compromise. It could exploit host access to escalate its privileges or gain persistence. |
| Recommendation: | Avoid installation unless absolutely required and the vendor is verified. |
Use of Reserved Ports
| Code: | host_port.block |
| Summary: | This error indicates that the application attempts to bind to one or more restricted ports (e.g. 443, ports reserved by the system or used for critical services). These ports are protected to prevent conflicts or security issues on the Industrial Edge Device (IED).
Reserved Ports:
22, 80, 443, 4443, 8081, 8443, 9443
2020, 2379, 2380, 4505, 4506
6443, 6783, 6784, 10250, 10255, 10256
|
| Recommendation: | The app developer must reconfigure the port usage to avoid reserved ports. |
Restricted Volume Mounts
| Code: | driver_opts.block |
| Summary: | This warning indicates that the application is configured to mount one or more restricted host directories into its container. These directories typically include sensitive system paths or runtime data that should not be exposed to applications. Additionally, usage of relative or path traversal characters such as ./, ../, $, or .\ is not allowed, as it may lead to unintended access outside the container context. |
| Recommendation: | Update volume definitions to use valid, allowed paths. |
Application Uses Layer 2 Network
| Code: | l2Network.warn |
| Summary: | This warning indicates that the application is configured to operate at the Layer 2 (Data Link Layer) of the OSI model, for example using MACVLAN or similar network drivers. This grants the application low-level access to the device’s network interface and allows it to send or receive Ethernet frames directly. Layer 2 access can be used to perform network sniffing, ARP spoofing, or other attacks. |
| Recommendation: | Use only if absolutely needed and vendor is trusted. |
CPU Core Reservation
| Code: | cpu_core_reservation.warn |
| Summary: | This warning indicates that the application requests exclusive CPU core allocation for certain services or processes. Reserving CPU cores can impact the overall performance and resource availability on the Industrial Edge Device (IED). CPU core allocation is typically required for real-time performance guarantees. |
| Recommendation: | Verify the app’s need for this reservation. Confirm the vendor is reliable. |
Exclusive NIC Access
| Code: | privilegedNicAccess.warn |
| Summary: | This warning indicates that the application is requesting exclusive access to a network interfaces (NICs) on the Industrial Edge Device (IED). Exclusive NIC access grants the application direct control over the network hardware, bypassing normal sharing and isolation mechanisms. Exclusive access may block other applications or system components from using the network interface. |
| Recommendation: | Confirm necessity with the vendor. Proceed only if they are trusted. |
GPU Resource Reservation
| Code: | gpu_reservation.warn |
| Summary: | This warning indicates that the application requests exclusive or shared access to GPU resources on the Industrial Edge Device (IED). Typical use cases include AI applications such as machine learning inference, as well as video processing tasks. |
| Recommendation: | Confirm the resource requirements and trustworthiness of the app provider. |